Managing technology implementation projects
It’s impossible to be an expert in every technology, but you can become an expert in managing change successfully and this requires a people-centred approach. Your employees will help give you a comprehensive picture of their needs and issues, so that these can be successfully addressed during the implementation process. Your people will then ultimately decide the success or failure with their trust or mistrust of any system.
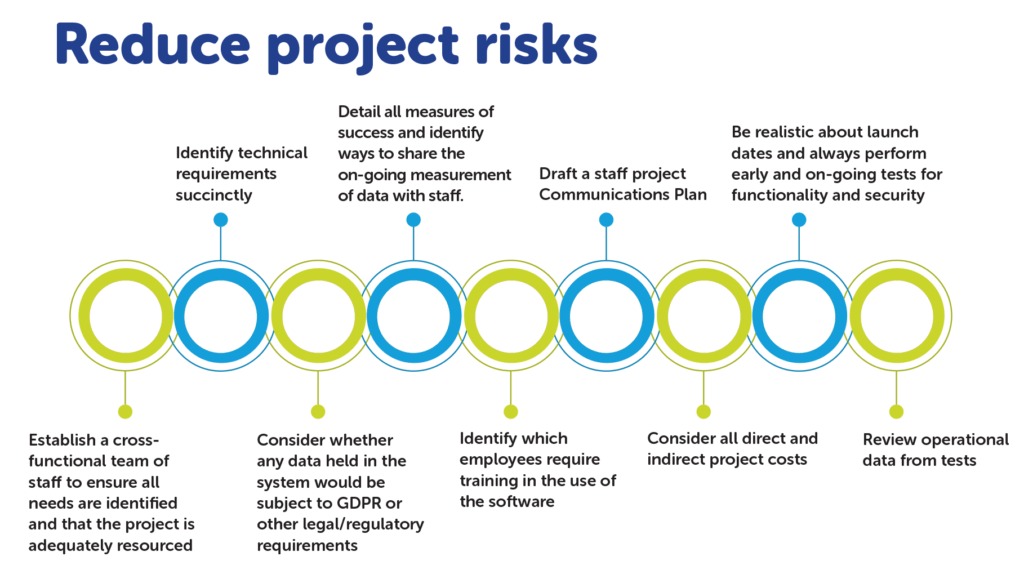
Fortunately, there are proven ways in which you can reduce these risks and improve the likelihood of success.
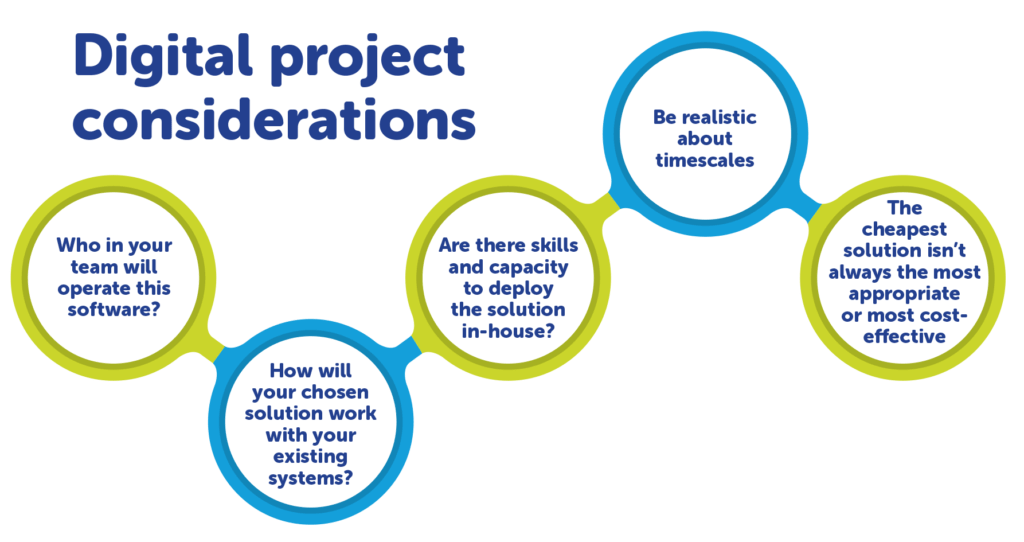
The key stages in managing technology implementation projects are:
- Identify requirements in a concise Project Brief
- Send Project Brief to prospective suppliers
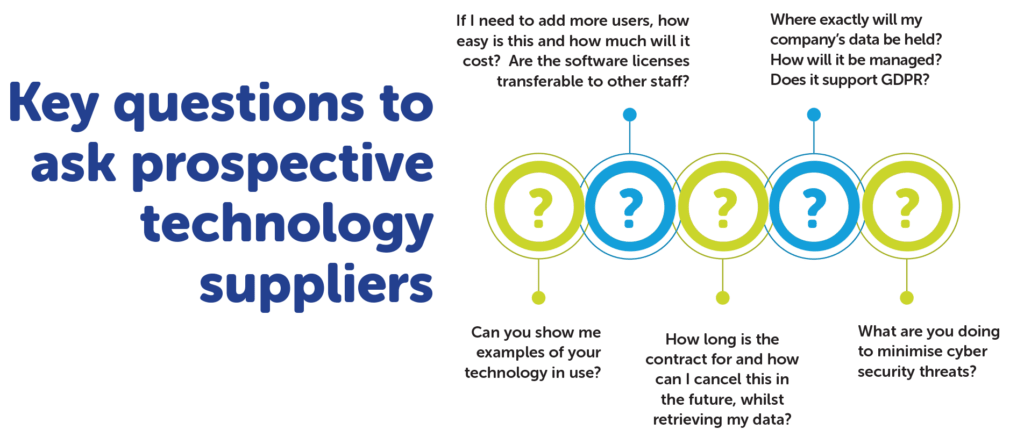
- Review all proposals against needs, costs, cyber security and small print T&Cs
- Get live demos and do financial due diligence on any suppliers before signing agreements
- Identify testing, training and ‘Go Live’ dates
- Resolve issues and maintain a Change Log
- Celebrate your successes. Be patient as they may take time to be realised